Ethical Hacker Hardik
Learn Free Ethical Hacking
Saturday, 25 November 2017
Sunday, 19 November 2017
What is Foot Printing (Hindi)
Foot-printing क्या है ?| What is Foot-printing?
Foot-printing क्या है ?(What is Foot-printing?)
आज हम हैकिंग में जो पहली परिक्रिया यानि की Foot -printing करेंगे । दोस्तों इसका नाम इसके बारे में बहुत कुछ बता देता है ,Footprint मतलब पैरों के निशान।ये बहुत ही जरुरी स्टेप होता है हैकिंग में।ये वो स्टेप होता है जिसमे हमे टारगेट के बारे में जितना हो सके जानकारी जमा करनी होती है। इस स्टेप के बाद हमे अपने टारगेट के बारे में कुछ information मिल जाती है । जैसे की जो System हमारा टारगेट है उसका IP(Internet Protocol) एड्रेस क्या है । ये वो एड्रेस होता है इसके मदद से हमे पता चलता है कि हमारे टारगेट कौन है । For Example :-
www.google.com = 74.125.68.104
ये google का IP एड्रेस है । इसी तरह हर System का अपना एक IP एड्रेस जरूर होता है । जिससे उसे पहचाना जाता है ।
www.google.com = 74.125.68.104
ये google का IP एड्रेस है । इसी तरह हर System का अपना एक IP एड्रेस जरूर होता है । जिससे उसे पहचाना जाता है ।
तो Footprinting कैसे होती है । इसको करने के बहुत सारे Options होते है लेकिन हम सिर्फ कुछ जरुरी ही Options को यहाँ पे पढ़ेंगे ।सबसे पहले मैं आपको फिर से बता दू कि Footprinting वो प्रोसेस है जिससे हम अपने टारगेट के बारे में जितना जान सके उतना ही फायदेमंद है ।तो आज हम अपनी इस Hacking की Class में Footprinting को कैसे करते है ये पढ़ेंगे ।
- By Search on Search Engine :- ये सबसे easy part है Footprinting का । इसमें हम अपने Target को किसी भी Search Engines पर सर्च करते है ताकि हमे उसके बारे में कोई काम कि डिटेल मिल जाए । Search Engine information का काफी अच्छ Source होता है जैसे कि Google, Bing, Yahoo, etc. आप कोई भी Search Engine इस्तेमाल कर सकते है ।
- nslookup Command :- इस command का इस्तेमाल आप कैसे भी कर सकते जैसे कि आप Linux या Windows use कर सकते है । इस Command को use करने के लिए आपको सबसे पहले Command Prompt Open करना है उसके बाद Type करना है "nslookup <website_name>" बिना qoutes("") के और Enter बटन दबाना है । जैसे कि निचे स्क्रीनशॉट में दिखाया गया है । For Example :-
अगर आपको एक वेबसाइट www.example.com के बारे में कुछ information चाहिए तो आप टाइप करेंगे :
nslookup www.example.com ये आपको उसका IP Address दिखा देगा । - Ping Command :- ये कमांड आपके टारगेट से Connectivity चेक करती है । मतलब ये कमांड चेक करती है कि जिस System को आप हैक करना चाहते है वो अभी चल रहा है या नहीं । चल रहा का यह मतलब ये ही कि वो Online है या Offline । अगर आपका टारगेट Offline है तो आपके लिए हैक करना लगभग नामुमकिन है । इस कमांड को इस्तेमाल करना भी काफी आसान है ।
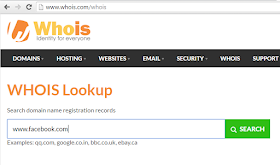
- Whois Lookup :- Whois Lookup Foot-printing में काफी Help करता है । अगर आपको किसी भी Domain (www.example.com) कि details चाहिए तो whois lookup best है । यहाँ से आप domain के owner की Details, Mobile Number, E-mail, Server, Etc की जानकारी ले सकते है । जैसे की निचे www.facebook.com की जानकारी दी गयी है ।
PING <target_address>
PING www.example.com
इन सब Techniques का आप इस्तेमाल करके अपने Target के बारे में कुछ Information पता लगा सकते है। Foot -Printing करने के लिए आपको Kali Linux में भी बहुत सारे tools मिलेंगे। उम्मीद है आपको मेरा ये पोस्ट पसंद आया होगा अगर आपको मेरा ये पोस्ट पसंद आया है तो Please इसे शेयर भी करिये।
इसके बाद हमे अपने Target के बारे में और भी जानकारी की जरुरत पड़ेगी क्योकि इतनी सी जानकारी के साथ हम ज्यादा कुछ नहीं कर सकते। आगे की जानकारी के लिए हम अगला Phase यानी कि Scanning पढ़ेंगे।
Friday, 10 November 2017
(Hindi) How To High Light Mouce Point
Namaskar Dosto Me Aj Fir Me ApbKe Liye Ek bhaterian toturial laya hun Jisme ap apne mouse pointer ko highlight kese kr sakte h.........
.............
To Chaliye Suru Karte H......
..............
1) Ap Ko Ek Shoftware Ki Jarurat Padegi Wo Aasani Se Google P Mil Jayege ga...
Es link pe click kr ne ke bad is Par Click Kr Na H......
Fir is pe click kr na h or is pe click karte hi downloade suru ho jaye ga......
Fir Ap Ki Downloade Path P Is Ka Install ApP Aajega ....
Fir Ap Ko Ise InstalL Kr Na H...........
.............
To Chaliye Suru Karte H......
..............
1) Ap Ko Ek Shoftware Ki Jarurat Padegi Wo Aasani Se Google P Mil Jayege ga...
Es link pe click kr ne ke bad is Par Click Kr Na H......
Fir is pe click kr na h or is pe click karte hi downloade suru ho jaye ga......
Fir Ap Ki Downloade Path P Is Ka Install ApP Aajega ....
Fir Ap Ko Ise InstalL Kr Na H...........
Is P Double Click Kr Ke Ap Ko Ise Open Kr Na H..............
Yahan Se Ap Apni Sabhi Setting Change Or Check Kr Sakte H..........
💡 Kr Right Side Wale Ko Agar Ap Press Kr ne Ke Bad Agar Koi Short cut Key Press Karenge To Wo Desktop P Show Ho gi
Free Ethical Hacking Or Computer Tricks Ke Liye Hamare Blog Ko Follow Karen
Thursday, 9 November 2017
(Hindi) Computer Challange Trick
Namaskar Dosto Me Aj Ap Ko Kuch Ese Challange Trick Bataunga JisSe Ap Kisi Ko Challange Karte H To 99.9 % Ap Us Challange Ko Jitenge ......
To Suru Karete H....
1) Kuch Ese Folder Name Jise Ap Kisi Ko Dange To Wo Us Name Ka Folder Ni Bana Sakta (ex.Con,Nul or blank name etc)
To Ap Ko Is Name Ke Folder Ko Banane Ke Liye 2 Codes Yad Rakhane Honge (0160,255) Ap In Dono Me Se Kisi Ka Bhi Use Kar Sakte H ...
Ap Ko Simple Folder Ka Name Dalne Se Phale (Alt) Button Babake Kisi Ek Code Ko Dalna H Or Fir Ye Name.......
.......
2)Blank Name Ka Folder Kese Banaye...
AP ko Bs ye Code Use Krna H Or Enter Button Press Krna H Bs blank Name Ka Folder Ban JAye Ga...........
.......................
3)Ek Hi Name Ke Do Folder Banane Ke Liye Bhi Ye Code Use Kr Na H.
.Free Ethical Hacking Or Computer Tricks Ke Liye Hamare Blog Ko Follow Kare
To Suru Karete H....
1) Kuch Ese Folder Name Jise Ap Kisi Ko Dange To Wo Us Name Ka Folder Ni Bana Sakta (ex.Con,Nul or blank name etc)
To Ap Ko Is Name Ke Folder Ko Banane Ke Liye 2 Codes Yad Rakhane Honge (0160,255) Ap In Dono Me Se Kisi Ka Bhi Use Kar Sakte H ...
Ap Ko Simple Folder Ka Name Dalne Se Phale (Alt) Button Babake Kisi Ek Code Ko Dalna H Or Fir Ye Name.......
.......
2)Blank Name Ka Folder Kese Banaye...
AP ko Bs ye Code Use Krna H Or Enter Button Press Krna H Bs blank Name Ka Folder Ban JAye Ga...........
.......................
3)Ek Hi Name Ke Do Folder Banane Ke Liye Bhi Ye Code Use Kr Na H.
.Free Ethical Hacking Or Computer Tricks Ke Liye Hamare Blog Ko Follow Kare
Sunday, 5 November 2017
How To Lounch TorJan Horse Attack (Part-2)
In my previous tutorial I discussed about the basics of trojan rat like what it is and how it work, In this tutorial we'll learn that how to launch a trojan horse attack.
their are many free trojan rats available on the internet but my personal favourite is Beast and pro rat for this tutorial I'll be using Beast 2.07
Lets start hacking:
Now send the server file to the person you want to hack (victim) and when he or she will install your server file on their computer-pc you will get email containing Their IP address and port number.
Now you can do all the things written on the right hand side of the software like looking at his/her webcams or at screen to see what are they doing.
Thank you guys, if are facing any problem in the making of the beast server please comm
their are many free trojan rats available on the internet but my personal favourite is Beast and pro rat for this tutorial I'll be using Beast 2.07
Lets start hacking:
- Download the beast 2.07 (click here)
- Run the Beast software from Beast2.07.zip.
- Click on "Build server".
- Now click on "Notification" button then click on "E-mail" in notification and in the E-Mail address column write your email address in that, ex- raj@blogspot.com.
- When you are done click of "AV-Fw Kill" button.
- Tick the "disable xp firewalls" in that.
- Now click on "Exe Icon" button and select one icon from that after that click on "Save Server".

Now send the server file to the person you want to hack (victim) and when he or she will install your server file on their computer-pc you will get email containing Their IP address and port number.
- Now enter the IP and Port no. which you got in email.
- Then click on "Go Beast" it will connect you to the victims PC.
Now you can do all the things written on the right hand side of the software like looking at his/her webcams or at screen to see what are they doing.
Thank you guys, if are facing any problem in the making of the beast server please comm
Introduction To Torjan Horse
Torjan or Torjan Horse is a Remote Administrative Tool (RAT). In simple words it is malicious/dangerous application which is used to get full control of others computer just by sending a file of several kbs to the victim and when the victim clicks on it he gives the full control of his/her pc computer to attacker.
Take their picture or make a video for their webcam.
Turn of their mouse or keyboard.
Shutdown computer.
Find the files in their computer.
Listen what they are speaking.
And many more things.
Thank you, if have any problem or doubt in understanding please comment. Here is the tutorial to download and use torjan horse
Let me make it easy for you :
Once upon a time there was a boy named B and he had a girlfriend G, one day B found G chatting to someone else so he decided to spy her computers for this evil deed he downloaded torjan software then using the torjan interface he created a small executable file name server.exe then he hided that server.exe behind the new pictures of his then he forwarded that picture to G and when G opened the picture torjan got installed on her computer because it was hidden inside the image. now once the server file was installed B got the full access of the G's computer.Below are the small list of thing You can do with torjan :
You can see what he/she typing.Take their picture or make a video for their webcam.
Turn of their mouse or keyboard.
Shutdown computer.
Find the files in their computer.
Listen what they are speaking.
And many more things.
Thank you, if have any problem or doubt in understanding please comment. Here is the tutorial to download and use torjan horse
Kali Linux Highly Compressed Free Download
hello guys today I'm sharing Kali Linux best penetrating OS right now as there are many people who don't have WiFi connection and downloading Kali is very difficult on their dial up connection because size of Kali is more than 2GB so here is the highly compressed Kali just 54.4 MB it can be downloaded on dial up connections.
Requirements to Extract this File:-
1) Win RAR
2) KGP Achiever
Download Link:
Phases Of Hacking
Every Ethical hacker plans his every hack and then performs the hack into certain stages and these phases are the most important part of any well planned hack because without any plan you will not know what to do next so in your journey of becoming an ethical hacker you should know these stages by heart.
1)Footprinting/Reconnaissance
Fooprinting or Reconnaissance is the first step of any well planned hack, In this stage hacker tries to collect's all possible information of the target that are available online, it includes stuffs like sub-domains,IP address, no.of host,emails,DNS,etc.
2) Scanning
Now after collecting some rich information of the target, hacker scans the target for vulnerablties, he performs many scans on the target to find out what kind of services are used by the target like searching the version of Apache server,operating system running on the box, open ports,firewalls detection and many more stuffs.
3) Attacking
On the basis of scanning results the hackers exploits vulnerabilities of the target, In simple words he/she attacks the victim on the weaknesses found while scanning for example; If there is fault in SQL database then hacker will do an SQL injection,If target is using the old operating system he will set a payload for it; If target has a less bandwidth then hacker will perform a Ddos attack and it keep on going with the vulnerabilities found.
4) Maintaining Access
After the attack got successful and all the information's of the company are copied, hacker setup a backdoor on the target machine which will help him/her to get information about the targets activities without getting caught, backdoor are fully undetectable(FUD).
5) Covering Tracks
When is done, when he/she has enough of the information of the target and thinks that they are done with hacking the target then they covers the track from which they comes in, by deleting logs, backdoor, uninstalling rat and reverting the changes made.
These are the stage/phases of hacking, which is the key for any successful hack always remember then always in your journey to ethical hacker, For any query and questions please commentShare to Facebook
How to Set Up A Hacking Lab
Welcome to the new lesson of Ethical Hacking course by Easy Hacks(EH), Today we are going to set up a hacking lab because every hacker needs an environment where he/she can practice their hacks and can test the systems to find vulnerability,loop holes, We are also going to do that by Installing Backtrack on Virtual Machine.
Importance Of Hacking Laboratory:
1) It will help you in learning to hacking practically because 90% of work is practical in hacking.
2)As a noob (beginners) you can't directly hack anyone because if you'll get caught, they will put you behind bars.
3) It needs lots n lots of practice in the starting to become a expert.
4) Every Hacker needs an environment where he can practice hacks and can test the different systems.
Below is the full video tutorial that how to make up a hacking lab on Virtual Machine.
If you have any questions or suggestion please
Social Engineering
Social Engineering is art of manipulating a person to give up his user id and password by building trust with him.
Social Engineering is one of the toughest hack because it requires great skills to gain trust of a stranger and once you gain the trust than it is most toughest hack to protect against.
How to perform Social Engineering..?
You can preform social engineering in million ways. Social Engineers perform their attack slowly as they gathers bits of information to create a big picture while some social attacks can be performed quickly over a phone call or a email. Method depends on your accessibility and ability.
But the process of social engineering is pretty basic.
1) Gather Information of victim
2) Build a trust
3) Use that trust to gain personal information of victim(id,password)
4) Use the information(id,password) of accomplish your goal
types of social engineering attack;
1) Phishing: Phishing is a technique to fraud a person via sending e-mail or text message to get the private/curtail information. Generally, phishers sends a mail that appears to come from authentic site like bank or form credit card website requesting a "verification" or "warning" and says to urgent log-in to link provided in that email and link takes you to the cloned website made by hacker appears to be original one, as you log-in your email address and password have gone in hands of hacker.
2) Bathing: In Bathing attacker leaves a malware infected "Pen-drive" or "CD-Rom" in the place where it conformed to be found by victim, as the victim finds it and insert that pen-drive or cd in his computer he install that malware unintentionally on his computer.
3) Pretexting: Pretexting is when one party lies to another to gain access to privileged data. for example, a pretexting scam could involve an attacker who pretends to need personal or financial data in order to confirm the identity of the recipient.
4) Quid pro quo: In Quid pro quo attack attacker requests information in exchange for something you want(gifts). what he does is quite simple, he create a survey with question asking your birth place and films you like many more question and when you complete the survey you can win a gift, so in exchange of these little gift he gets all the information about you and from you.
5) Tailgating: In tailgating an unauthorized party follows an authorized party into an otherwise secure location, usually to steal valuable property or confidential information. this often involves subverting key-card(pass) access to a secure building or area quickly following an authorized user and catching the door or other access mechanisms before it closes.
6) Others: there are many more types of social engineering attacks like "diversion theft" mostly performed on transporting companies and "Phone Phishing" it is same as Phishing just performed over a phone call and many more are there let me tell you Social Engineering is a vast subject it is different from all other hacking techniques on this site.
Note: You can get certified in social engineering some sites offer one week course and after that test to make you "certified social engineer"(CSE).
Networking Topology
In my previous tutorial I wrote about Introduction to Networking In this tutorial we'll discuss about Networking Topology, The computer can be connected to one another in several ways. These ways of networking are called Topology.
The three main of Topology are given below:
1) Bus Topology
2) Star Topology
3) Ring Topology
Remember:Client is a computer connected with the sever though a cable that can access information stored on the server. It is also known as Node.
1) Bus Topology
In this topology, the server and the rest computer (called Clients) are connected to a single cable for communication called the bus. it is less costly because it uses less cable but it has a drawback that if the bus fails the entire network fails.
2) Star Topology
In this topology, the computer called clients are connected to a hub that is directly connected to a central computer called server. The server manages and controls all the communications between the clients. All the clients depends on the server because if the server fails, the entire network fails. if a client fails, rest of the clients are not affected.
3) Ring Topology
In this topology, the computers are connected to one another though the ring cables, the information travel from one computer to the next computer to reach its destination. draw back of this topology is it one computer fails entire network of computer fails, it is cheap ways.
Thank you for reading and keep reading for more tutorials like this, Comment if you have any questions.
Subscribe to:
Comments (Atom)
Get Complete Html Tags
Get Complete All Html Tags Downloade Pdf by Here >>> Click Here
-
Get Complete All Html Tags Downloade Pdf by Here >>> Click Here
-
Torjan or Torjan Horse is a Remote Administrative Tool (RAT). In simple words it is malicious/dangerous application which is used to get ...















.JPG)

.JPG)

.JPG)
.JPG)


